Right now there are 43 million working women in the United States. While the feminization of the workplace is good news for women seeking to establish a career, it has created a significant shift in our understanding of family and gender roles. The traditional expectations placed on women to raise children and tend the home have eroded, and while this has granted freedom to women, the fact is that child rearing is a necessary part of life. With more women choosing to make their careers a priority, the task of raising children is now falling on a relatively new and untested mother: the child care system.
There are about 20 million children between the ages of 0 and 4 in the United States, and around 13 million of them are enrolled in regular child care. There are 819,000 daycare facilities nationwide, varying from nannies and small neighborhood operations to large-scale facilities. Enrollment may be expensive, costing up to $16,000 per year (depending on the location and level of care). In total, the United States will spend about $70 billion on child care in 2013, which averages to $5,384 per child. This may not seem like an extraordinary amount of money, but with nearly 30% of families headed by only one parent, and the median annual income for single mothers being a mere $32,000, child care can become a serious expense.
Many parents note that, apart from affordability, there are availability issues that often require them to place their children on waitlists. Although the child care industry continues to grow, it’s failing to meet the demand. This puts parents in difficult situations, sometimes forcing them to choose between working and caring for their children. Because of this, many parents are forced to use unregulated child care, which has resulted in some alarming stories of neglect, abuse and even death. In a recent interview, The New Republic’s Jonathan Cohn summed up the state of child care this way, “We have this awful situation where the daycare we have isn’t good enough, and yet it’s also too expensive for many families to afford.”
In a somewhat ironic turn of events, women are increasingly finding themselves turning to child care as a career. A vast majority of child care workers, upward of 95%, are female. With 1.5 million women professionally caring for children, perhaps the migration of women into the workplace is less of a liberating endeavor than initially thought.
A possible solution to these issues could be to replace child care facilities with child care factories. Fully automated, open all hours and built to meet standardized health and safety requirements, the child care factory uses modern industrial machinery to streamline the process of caring for young humans. Although mechanization may be a nemesis of job creation, it’s worth noting that the influx of 43 million women into the labor force did not collapse the job market.
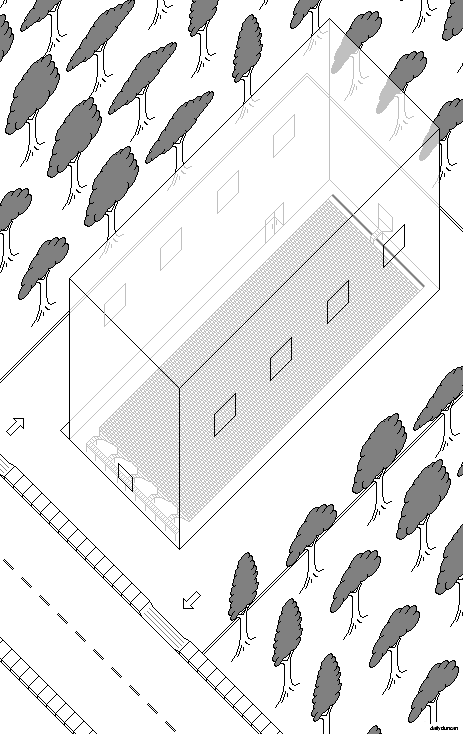
The above image is an example of the general layout of a child care factory. Parents enter the lot in their vehicle, drive around to the rear of the building and place their children in the drop-off window. After doing so, the parent receives a receipt later used to obtain the child. Once placed in the window, the children are then stripped, tagged and cataloged into inventory while gleefully tumbling along a conveyor belt before plummeting a short distance into a large ball pit. The children, or items, then spend the duration of their visit blissfully suspended in the pit while a mixture of classical music and educational material plays from speakers overhead.
While in the pit, cameras capture the events while the items’ vital signs are monitored by the tags they received upon entry. If an item exhibits an abnormal heartbeat, breathing rate or other signs of medical crisis, they would immediately be removed from the pit, and the appropriate parties would be notified, whether that be the parents, paramedics or supervising factory staff. Also, if a parent was inclined to check the status of their child, they could monitor the factory’s inventory on the company’s website or call an automated answering service, which would politely guide them through a series of unnessecary options.
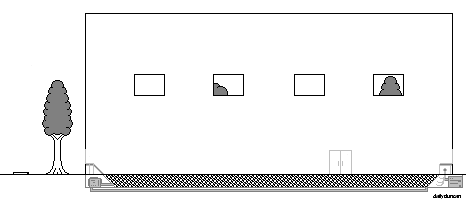
The side view above shows some of the inner workings of the factory, including the ball-sanitation pump, which continuously removes and sterilizes the plastic balls before returning them to the pit. Also visible is the dredging claw and pneumatic cylinder. The claw is comprised of a pleasant, robust material as to avoid damaging children as they are gently snared in its soothing hooks.
The items also receive nourishment from the nutritious coating that is continuously applied to the balls after cleaning. This solution provides the perfect balance of vitamins, minerals, fat and protien that a growing child requires. And since children can’t help but attempt to put everything in their mouths, they actually feed themselves.
When a parent is ready to pick up their child, they simply drive through the pickup window and scan their receipt. The item is then located using tag and a portion of the claw extends to dredge them from the pit. The item is then placed on a conveyor belt and sanitized before appearing at the pickup window along with its clothing. The parent then places the child in the vehicle and continues about their business.
Industrialization has proven to increase safety in areas such as food production and product assembly, so it seems feasible to entrust our offspring to its lifeless, metallic arms. After all, we never leave prized possessions with strangers.